Setup an Onion Email
with Thunderbird
Introduction
In today's digital landscape, privacy and anonymity have taken center stage, especially when it comes to email communication. The Darknet—often referred to as the hidden side of the internet—relies heavily on the Tor network and onion addresses to maintain user anonymity. By using an "Onion Email" address, your email traffic travels through the Tor network. This masks your IP address and makes it harder for anyone to trace your identity or location. This guide will show you how to set up and configure Thunderbird with an onion-enabled email account, so you can then leverage the Darknet’s privacy benefits for your everyday communications.
Understanding How The Tor Network Works
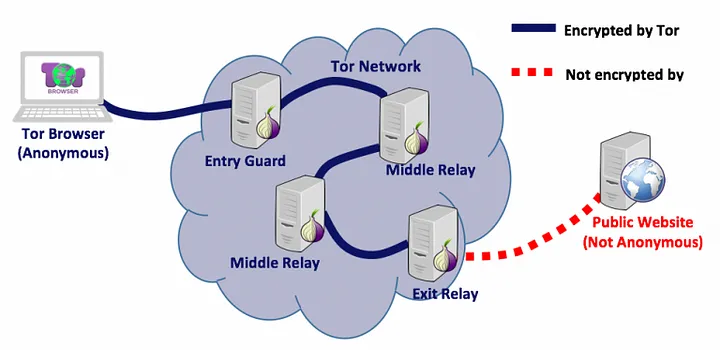
The Tor network relays your internet traffic through a series of encrypted nodes. Each node only knows the previous and next step in the chain. This layered encryption ensures no single entity can uncover your real IP address or ultimate destination.
How Onion Routing Ensures Privacy
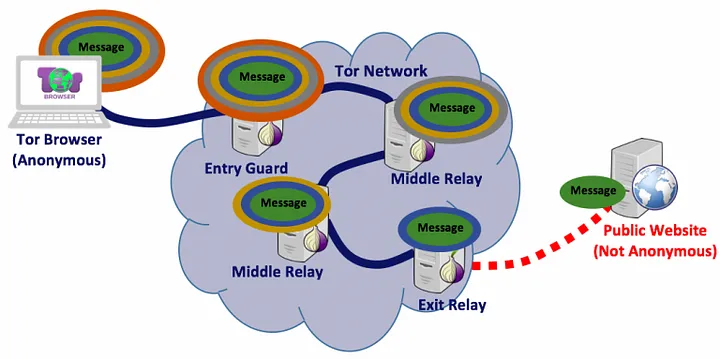
Tor uses a multi-layer encryption process, often described as onion-like, for each data packet you send. When a relay peels off one layer, it only learns where to forward the packet next, without seeing previous hops or the final destination. Because no single relay knows the entire path, it becomes extremely difficult for anyone to trace or analyze your traffic. This layered approach offers robust privacy, keeping your identity and browsing habits hidden.
Benefits of Onion Email
An onion-based email service keeps your identity hidden by operating entirely within the Tor network. Because your email traffic never leaves Tor on your end, it reduces the risk of IP leaks through traffic analysis. At the same time, such services can still exchange messages with regular email providers, because the final “hop” to the clearnet occurs on the server side rather than your own connection. This blend of complete Tor-based anonymity and compatibility with standard email addresses offers robust privacy without sacrificing everyday communication.
Even if a communication partner is arrested and your email address falls into the hands of a repressive regime, and XMR.email were forced to hand over account information, it would be technically impossible for the provider to disclose any IP addresses—simply because they do not have them. XMR.email relies entirely on the Tor network and does not record any IP data that could be used to identify you.
In other words, all data traffic takes place within Tor, which makes your real IP address invisible to the provider (and, therefore, to authorities or other third parties). Under the greatest pressure, the operators could not turn over IP information, because they simply do not possess it.
Configuring Thunderbird
Initial Thunderbird Setup
Before we start configuring Thunderbird, we first need to install tor on Linux you can do this with the following commands. On Windows you only need to download and start the Tor Browser, otherwise Thunderbird on Windows cannot connect to the Tor network.
To install Tor on Linux:
Now we just have to start Tor and set it to autostart, then we can start setting up Thunderbird.
sudo systemctl enable tor
Adjusting Tor Proxy Settings
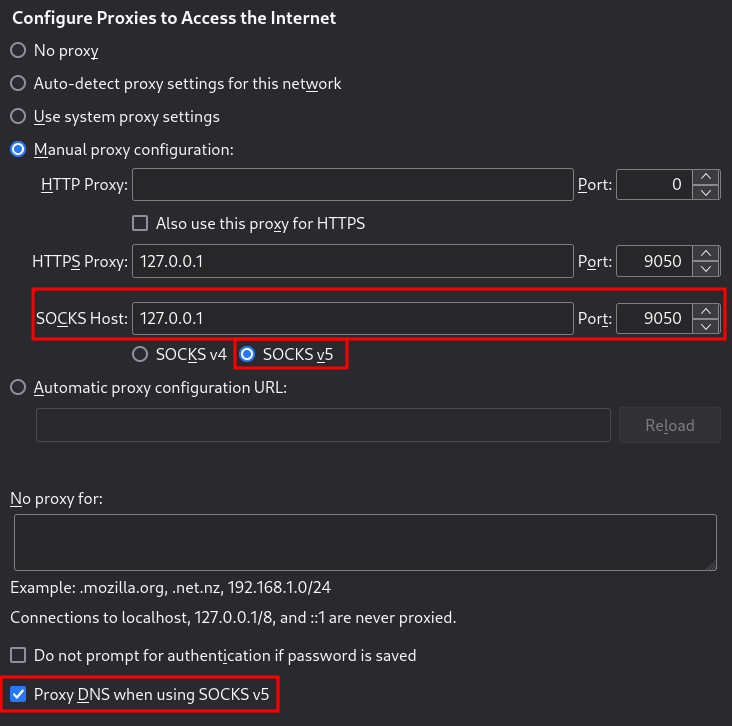
To get Thunderbird to work with .onion domains / hidden services we have to set a proxy in thunderbird. This is done as follows:
- Go to "Connection Settings"
- Select "Manual proxy configuration"
- Set HTTPS Proxy to: 127.0.0.1 and port 9050
- Set SOCKS Host to: 127.0.0.1 and port 9050
- Select SOCKS v5
- Activate "Proxy DNS when using SOCKS v5"
Adding a New Email Account
To use your onion xmr.email account in Thunderbird, create an account in Thunderbird as usual. Here is an example configuration:
- Your full name: ENTER SOME RANDOM SHIT
- Email address: test@xmr.email
- Password: ***********
- Tick "Remember password"
- Incoming Server
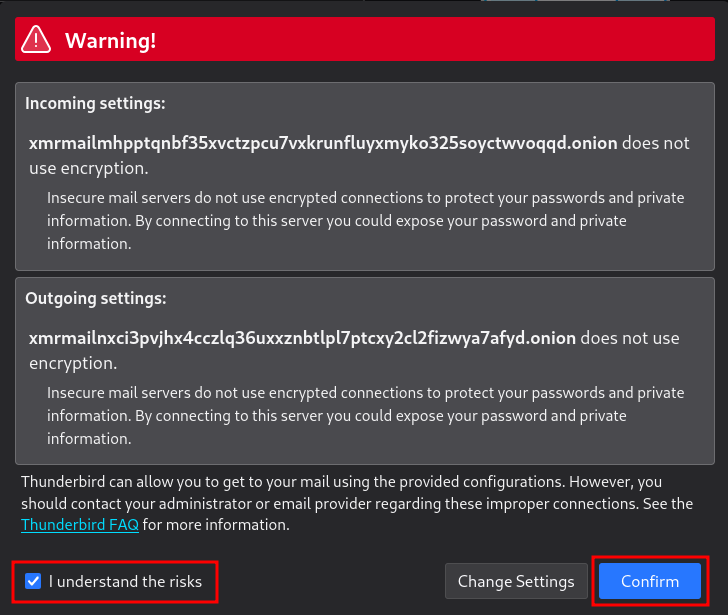
- Protocol: IMAP
- Hostname: xmrmailmhpptqnbf35xvctzpcu7vxkrunfluyxmyko325soyctwvoqqd.onion
- Port: 143
- Connectivity security: NONE (We don't need it since Tor is already end to end encrypted.)
- Authentication method: password
- Username: test@xmr.email
- Outgoing Server
- Protocol: SMTP
- Hostname: xmrmailnxci3pvjhx4cczlq36uxxznbtlpl7ptcxy2cl2fizwya7afyd.onion
- Port: 143
- Connectivity security: NONE (We don't need it since Tor is already end to end encrypted.)
- Authentication method: password
- Username: test@xmr.email